Zero-day lexicography
« previous post | next post »
It was reported yesterday that Microsoft has released a patch for a recently uncovered flaw in Internet Explorer. Thus Fahmida Rashid, "Microsoft Releases Emergency IE Patch", Security Watch 9/21/2012:
Microsoft has released an out-of-band update fixing at least five vulnerabilities in Internet Explorer, including the recently disclosed zero-day vulnerability already being exploited in the wild. [emphasis added]
If you don't know what a "zero-day vulnerability" is, Wikipedia will explain it to you:
A zero-day (or zero-hour or day zero) attack or threat is an attack that exploits a previously unknown vulnerability in a computer application, meaning that the attack occurs on "day zero" of awareness of the vulnerability. This means that the developers have had zero days to address and patch the vulnerability. Zero-day exploits (actual software that uses a security hole to carry out an attack) are used or shared by attackers before the developer of the target software knows about the vulnerability.
It's worth noting in this case that the vulnerability in question was still called "zero day" after being in the news for almost a week: it seems that zero day has come to mean something like "known to bad guys before a defense is available".
In any case, I'm curious about where this whole "zero day" business came from, and how widely it's spread.
The OED has zero day glossed as "Mil. the day on which an attack or operation is scheduled to begin", with citations back to 1929:
1929 Papers Michigan Acad. Sci., Arts & Lett. 10 335/2 Zero day, the day for an attack.
1938 Brit. Jrnl. Psychol. 28 325 On zero-day (the day preceding the beginning of training with the aid of the electric shock) each rat was immersed six times in the tank.
1947 L. Hastings Dragons are Extra iv. 80, I..fixed a zero-day three months ahead.
1978 R. V. Jones Most Secret War xxxix. 350, 20th October had been fixed as Zero Day for rocket attacks on London to begin.
This is just above the more familiar zero hour "Mil. the hour at which an attack or operation is timed to begin". The recent computer-security usage drops the whole idea of an attack or operation scheduled in advance. It retains the idea of counting days from zero in an attack or operation — except that you never count past zero. On the day after a zero-day exploit appears, it's not called a "day one exploit" or whatever.
The oldest clear examples that I've found of zero day in the current computer-security sense are from 1999-2001. A whitepaper which claims to have been "originally published in 1999" — Ron Gula, "Broadening the scope of penetration-testing techniques" — has a section on "Zero-Day Exploits". And Brian McWilliams, "Lapse At SANS May Have Been Self-Inflicted", Newsbytes 7/16/2001, has:
The computer security research and education group restored its Web site Sunday evening, after its home page was replaced Friday by an attacker using the name "Fluffi Bunni." The defaced page included a photo of a pink stuffed rabbit in front of a computer. On the screen of the monitor read a message, "Would you really trust these guys to teach you security?" […]
"This was probably a procedural failure, where somebody left something exposed. I don't think this was the result of a zero-day exploit," said a source close to the organization. Zero-day exploits are closely guarded vulnerabilities discovered by attackers in popular software but not published widely.
It's pretty clear that people in the biz used this term for a while before that — but for how long? Where and when did it start?
And there are some sporadic examples of analogous uses in other fields, such as "zero day inspections". Thus the Lexington Dispatch for 9/17/1996:
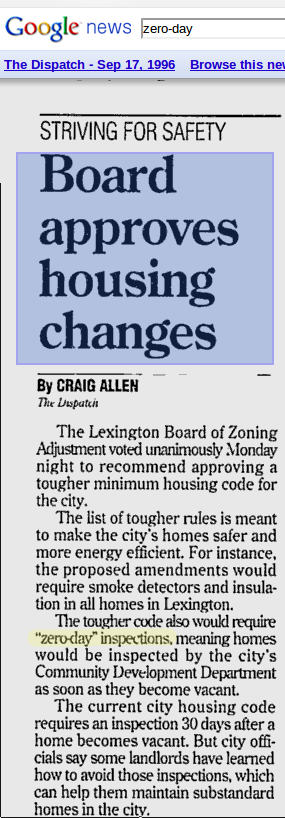
[Update — in the comments, Sifu Tweety points to this item, said to be a transcript of an 8/7/1992 TV news story, containing this quote from Glen Vermette of the Victoria City police:
I've never run across a case where, uh, you phone up one of these pirate boards and they say I want X amount of dollars for this program, it, it doesn't happen. They do it, it's more to gratify their ego, is what it is [grins] um, the big kick seems to be if you can get what's called zero day wares (they call them wares, for programs) uh, meaning that the day it's released, they've got them available to download, or in a lot of cases, uh, if they can the program even before it's released to the, duh, general public, all the better.
In this case, "zero day" refers to the availability of pirated software relative to the release date of the authorized versions. Brian B cites a similar usage, with the difference that "a 'day-zero' leak (/crack/whatever else) is a leak before the product is released", while "if it's pirated the day it comes out (but not before), that's a 'day-one' leak".]
The current collocational propensities of zero-day are indicated by the following counts from Google News during the past month:
| zero day vulnerability | 68 |
| zero day exploit | 57 |
| zero day flaw | 25 |
| zero day attack | 11 |
| zero day threat | 5 |
It's a little surprising not to see any figurative extensions of zero day outside the realm of computer security. Are there zero-day personality flaws? Zero-day relationship attacks? Zero-day marketing exploits? Apparently not.
Nancy Wright said,
September 22, 2012 @ 8:53 am
I understand that in thru-hiking, the term "zero day" is a day when you do no hiking. Typically it's a day spent in a town hear the trail, where you can take care of laundry or supply issues. This usage is not precisely analogous to what's being discussed here; but it IS out there.
Brian B said,
September 22, 2012 @ 9:28 am
I don't think this usage is related at all, but in piracy/anti-piracy terminology, a "day-zero" leak (/crack/whatever else) is a leak before the product is released. Related to that, if it's pirated the day it comes out (but not before), that's a "day-one" leak.
Sifu Tweety said,
September 22, 2012 @ 9:39 am
Zero-day was originally hacker slang, and got carried over to computer security with the professionalization of hacking culture. If you're interested in a (not terribly well dated) corpus to search for earlier occurences, I would recommend the textfiles.com corpus of early (early '80s BBS era through maybe mid-2000s?) hacker/computer underground writings. If I do a search there I find a couple of earlier examples in the early search results; BoW #6 (the first result) is dated (within the text) to 1994, and this file purports to be a transcription of a TV news piece from 1992. Personally I remember the term from the late '80s, used mostly in reference to warez (that is, pirated software), but I imagine it predates my experience with it.
Sifu Tweety said,
September 22, 2012 @ 9:43 am
And Brian's usage tracks with my memory; it referred to software that was available illegally for download on BBSs prior to its commercial release. The usage in reference to computer security referred to exploits that had been found but which were not yet publicly traded or discussed on BBSs.
This is all my memory of things; I don't have any particular empirical data to back it up, although I suspect that can be found in the textfiles.com archive someplace.
Ambarish Sridharanarayanan said,
September 22, 2012 @ 10:25 am
Just pointing out that the name of the first writer quoted seems to be Fahmida Rashid. Given this is Language Log, should I venture that the typo could be influenced by the more common name "Fatima"?
[(myl) Fixed now. Another data point for someone's collection of digital lapsus calami.]
Tony Spataro said,
September 22, 2012 @ 11:47 am
I started using computer networks in 1990. At the time, few computers outside of universities and labs were connected to the Internet. For most computing enthusiasts "network" referred to either a local-area network, or a dial-up bulletin board system (BBS) that was connected to other systems by a store-and-forward phone link. In this environment, most malware consisted of inert viruses as opposed to self-propagating worms.
Fast-forward to 1995 when Internet usage among private citizens began to ramp up. Suddenly, everyone's desktop PC was connected to a global packet-switched network and constantly sending and receiving data in the background, said data being processed by a software networking stack; software has bugs, and some of these bugs are exploitable vulnerabilities.
With the advent of Web and dynamic content (e.g. JavaScript) in the late 90s, malware malware becomes dominated by self-propagators such as worms and browser exploits. It was around 1997 that I first saw "exploit" and "zero-day" used in their modern sense by the media, as an exploit that has just been discovered.
However, "zero-day" as used by security researchers has a somewhat more specific meaning. Consider that an exploit (piece of malware) relies on a vulnerability (software bug) to do damage. "Zero-day" refers to the time elapsed between public disclosure of the vulnerability, and discovery of the exploit for that vulnerability.
In other words, a zero-day attack relies on a vulnerability that the bad guys discovered BEFORE the good guys. That's what makes them so insidious: there's no way to defend against them, regardless of how diligently one updates his software packages and malware defenses.
L said,
September 22, 2012 @ 11:58 am
Perhaps if you substitute the more generic "time zero" as used generically in science and engineering, this will all make more sense. An event at t0 is an event "at the very beginning" or "at the reference moment."
We've all sat and watched rocket launches count down from "t minus ten seconds" (or whenever) – this is "negative time" or "time before the zero point" which in that case is the launch.
Think of 11 pm as "tomorrow minus an hour" and suddenly midnight becomes "zero" – as again, is used by the military etc.
One unusual usage that didn't work this way, was the launch of the Normandy Invasion – planned well in advance, to be launched at H hour of D day (presumably falling in M month of Y year).
J. L. Barnes said,
September 22, 2012 @ 12:23 pm
I wouldn't be surprised if you weren't able to find usages of "zero-day" in terms of pirated software (commonly referred to also as "warez") dating farther back than 1992. It may be in the form of "0-day" or even "z3r0-d4y w4r3zzzzz#@!#!@111" but I'm sure it's there, possibly as early as the mid-80s.
Steve Tauber said,
September 22, 2012 @ 12:48 pm
I've been involved with the hacker scene for over a decade now and originally heard this term spoken as "oh day". Essentially 0 (zero) being read as O (letter). I haven't checked but I wouldn't be surprised to find some references as "oh day", O-day, 0-day, etc.
Martin said,
September 22, 2012 @ 11:05 pm
Computer programmers count from 0, at least the kind that do security.
Nick Lamb said,
September 23, 2012 @ 4:16 am
I just skimmed the earliest printed/published material I own (the 1985 book by "Hugo Cornwall") about this subculture and it has no indexed or readily visible mentions of "zero day".
The use in illegal copying of video games, and particularly in the defeating of copy protection features ("cracking") and subsequent distribution might indeed pre-date the security concept as suggested above, and those two cultures overlap thanks to shared interests in how things actually work and can be subverted to do what you want rather than what was intended.
In terms of documentary evidence, "crack intros" might be a good source. These are small programs which run while a cracked video game is loading, they may be cover for some actual work needed to defeat the protection each time the game runs, but more often they just reflect the long loading times associated with floppy-disk based games in that era. They are laden with teenage boasting, so somewhere there will be a crack that's the first one to mention "zero day" or "0day" or similar words because as soon as one person in the scene heard that phrase they'd want others to know they were familiar with the slang.
peterv said,
September 23, 2012 @ 6:50 am
"Computer programmers count from 0, at least the kind that do security."
How, precisely, is it possible for anyone to count zero objects?
And how, bizarrely, is it possible to assign the label known as "0" to the first object in a collection of more than one object?
[(myl) The point at issue is how items in an array are indexed. Mathematicians generally count from 0: e.g. x0, x1, x2, …
Many programming language count from 1 — in Fortran, Matlab, and R, for example, the first item in array X is X(1) or X[1] or whatever. But in some other languages, such as C, arrays are indexed from 0.
For one take on the argument, see Edsger Dijkstra, "Why numbering should start at zero", 8/11/1982.]
Rod Johnson said,
September 23, 2012 @ 7:22 pm
I also remember zero-day cracks in the warez scene in the mid-90s. I was thinking I first saw it on Hotline, but Hotline dates from 1997 and I'm sure I saw it before that–perhaps on IRC. Such things by their nature are ephemeral and rarely archived, so it may be hard to definitively establish early uses.
a George said,
September 24, 2012 @ 4:15 am
I have a different problem with “zero”, and I have been unable to crack it. The background is the following: during most of WW2 official Denmark was cooperating with the German occupation forces and authorities; however individual groupings were not. An organisation called “Free Danes” created an independent propaganda office (“The Information Office of the Danish Council”) in London to promote Danes as opposed to official Denmark. One of their pamphlets was called “Danes stand to for Zero”. I can make no head or tail of this title. Its content does not give a clue. I can stand to attention, and if I had been a military man, perhaps to other things. But zero?
Bill said,
September 24, 2012 @ 8:53 am
"How, precisely, is it possible for anyone to count zero objects? "
We're not counting objects, we're labeling items in a list, and we can label them any way we want to, as long as everyone agrees on the system. Call them
1,2,3
0,1,2
I,II,III
Monday,Tuesday,Wednesday
Huey,Dewey,Louie
The WWII usage precedes computers, but the programming convention may explain why hackers adopted the terminology.
David Letterman calls his first item "10."
Joe said,
September 24, 2012 @ 9:50 am
@Tony Spataro: "'Zero-day' refers to the time elapsed between public disclosure of the vulnerability, and discovery of the exploit for that vulnerability."
Actually, a vulnerability retains its zero-day status until a fix to remove it is published. Sometimes a zero-day is discovered via an exploit (eg, some stuxnet attacks exploited a couple of microsoft zero-days). In fact, most security software (eg, anti-virus) rely on the signatures of the exploits to provide a line of defense against zero-day attacks.
Dennis Paul Himes said,
September 24, 2012 @ 9:52 am
@Nancy Wright: Through hikers generally just say "zero", without "day", as in, "I'm going to take a zero on Thursday." They'll also use "zero" as a verb, as in "I'm going to zero in Monson".
boris said,
September 24, 2012 @ 2:27 pm
Speaking as a programmer, Dijkstra's explanation is not convincing. In real life, if there are X objects, you label them from 1 to X where object X is the Xth object in the sequence (VB.NET manages to both start at zero AND make it so that object X is the Xth object, which makes for extreme confusion. If you declare an array with zero elements, it in fact has one element at position zero). You get used to it, though.
I always thought the use of zero here is more related to the use of the binary system in computers, and was later generalized to base 10. Zero is the smallest unsigned integer, so start with that. But this doesn't apply to array indexing. The only thing I can think of where this becomes useful is that in languages like C you can dereference a pointer to an array to get elements starting at that point so that if X is an array *X starts at the first element of the array, *(X+1) starts at the second and so one. In this case it makes sense to say that *(X+0) = X[0] and therefore start counting at zero. But high-level languages shouldn't worry about things like this.
[(myl) I'd argue that indexing from 0 make you much less likely to make off-by-one errors in implementing something like convolution.]
Brad Daniels said,
September 24, 2012 @ 4:00 pm
I remember walking down the hall at DEC's facility in Nashua (near the C compiler group) back in 1988 and hearing one developer say to the other "that puts us right back at square zero". I knew then that I had found my people.
M (was L) said,
September 24, 2012 @ 4:34 pm
@peterv
> And how, bizarrely, is it possible to assign the label known as "0″
> to the first object in a collection of more than one object?
We do it precisely as you suggest: bizarrely. We are a bizarre breed, though neither you nor I are the first to say it.
There is no zeroeth element of an array; however the first element might be indexed as zero.
There is, on the other hand, a Zeroeth Law of Robotics, and had Asimov lived longer, there might even have been a Negative First Law.
There's a whole lot of Fahrenheit below zero.
Mark said,
September 25, 2012 @ 7:30 am
@boris As a programmer who worked in assembler and low level languages I find his logic pretty strong. When you're manually building a structure in memory (48 bytes of memory for 24 16-bit integers) you write down the starting memory location and then add offset data to that address to get to the various data locations. Since you don't want to waste bytes you use "0" for the first location so that when you shift-left (multiply by 2 to get the even offset required for 16-bit in a byte world) and then add you wind up with the initial address.
0-offset arrays become habit real quick because anything else surprises and confuses other people AND eats up valuable extra bytes of code-space.
Worse, when counting down, many processors only had "JMZ" and "JMNZ"… you could only if-branch on matching zero or non-zero. So you do a lot of working backwards where you work on 16 items using 15..0 and doing a JMNZ at the end of the work block to jump back to the beginning when not zero.
RP said,
September 25, 2012 @ 12:36 pm
@boris,
You say that in VB.NET, "If you declare an array with zero elements, it in fact has one element at position zero". This isn't really true. If you declare Dim x(0) then you're declaring an array with one element. You are assuming that (0) is meant to be the number of elements. It's not; it's the upper bound. You only see that as illogical because you look at VB.NET through C or C-style spectacles.
I've never used a Basic where the syntax was Dim array(length), though there may well be one (since there are countless dialects). Historically of course, some Basics did have a lower bound of 1, and Microsoft Basic offered a choice of default lower bound (0 to 1) as well as the option to have a completely different one (e.g. Dim(1500 to 1700) if you wanted an array where the lowest index was 1500 and the highest index was 1700).
Svafa said,
October 4, 2012 @ 4:12 pm
Building on Brian B's comment, I've also seen pre-launch/release leaks referred to as negative-day, rather than zero-day or day-zero. This typically refers to pirated programs/music/videos that are available before their official release, while hacks/cracks are more often referred to as zero-day due to being available at release.
@Dennis and Nancy: I've heard both zero and zero-day used frequently by thru-hikers, sometimes interchangeably within the same sentence. For instance, "We had a zero-day on Thursday, so we figured, hey, why not zero Friday too?". However, I don't think I've ever heard zero-day used as a verb. And, as noted, the trail usage is not related to the one being described in the post here.
Andrew said,
February 5, 2013 @ 12:31 pm
"There is, on the other hand, a Zeroeth Law of Robotics, and had Asimov lived longer, there might even have been a Negative First Law."
In one of the authorized sequels to the Foundation books, there was a Negative First Law